DNS over HTTPS - What's it all about?
By Mark Amory, Cyber Curriculum Lead
A little bit of background for you. Back in 2017, Mozilla started trialing support for DNS over HTTPS (DoH) using their Firefox browser. Then earlier this year they started to roll out DoH in their browser as an optional feature. In the Autumn of 2019, Mozilla will begin the roll-out of their browser with DoH enabled by default. This roll-out will become global throughout 2020.
This week saw Google start their own DoH tests with Google Chrome. At the moment, Chrome users have to add a statement at the end of the .exe for a browser to use DoH. Yet, what we will see, in future releases is a button-click, like Firefox.
How to enable DoH in Mozilla Firefox?
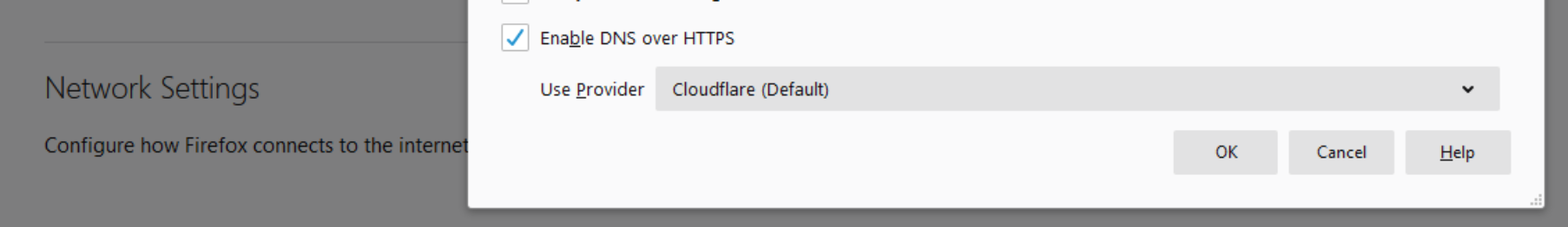
Until it becomes the default setting you will need to follow this simple process. Access the options for the application (tools→options). Scroll to the bottom of the General settings and access the Network settings. At the bottom of the pop-up, you will find the option to enable DNS over HTTPS.
How to enable DoH in Google Chrome?
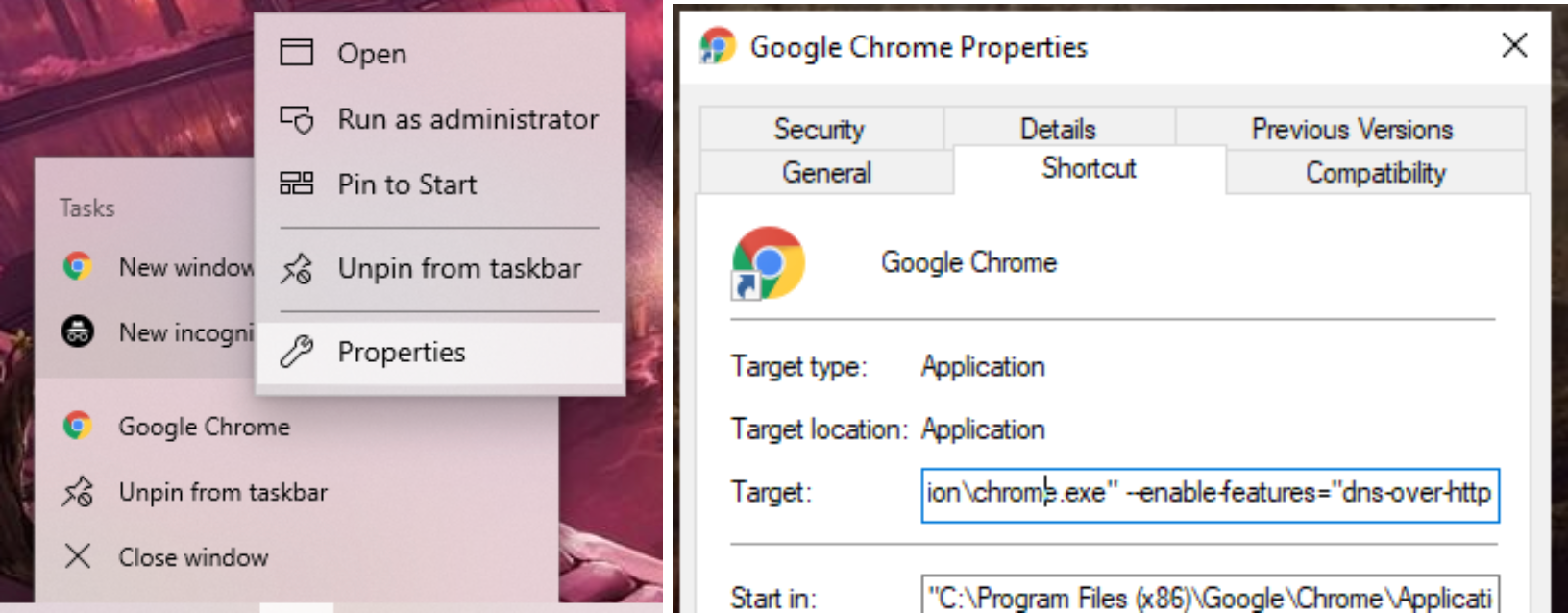
To allow Google Chrome to use DoH you will need to access the properties for the application. Then add the following text to the target field:
--enable-features="dns-over-https<DoHTrial" --force-fieldtrials="DoHTrial/Group1" --force-fieldtrial-params="DoHTrial.Group1:server/https%3A%2F%2F1.1.1.1%2Fdns-query/method/POST
What are the benefits for users?
When using traditional DNS, your device sends plain-text UDP queries across the network to a DNS server. It then awaits a response. These queries and responses can be intercepted by Network Administrators, ISPs, Hackers and Intelligence Services. They can all determine your browsing actions. These people can then do many things to your browsing session:
- They can block the responses, ultimately stopping you from browsing to your desired site.
- They can supply altered responses. Forcing your browser to connect to fake, or malware-filled sites.
If your DNS queries are encrypted, all these threats are immediately rendered inert.
Criticism over DoH
There has been a fair amount of criticism on the use of DoH from some parties.
Criticism was levied against Mozilla only allowing DoH enabled versions of Firefox to send DNS queries to Cloudflare. This meant that users had no choice of DNS providers. This meant that CloudFlare had an unfair advantage, over others.
Mozilla has now responded to allow users to specify their own DNS provider in the DoH settings.
Additionally, Cloudflare have issued a privacy notice (outside their normal privacy notice). Stating that they will not utilise any DoH related data for anything other than improving the DoH service.
The Internet Watch Foundation (IWF) and the Internet Service Providers Association (ISPA) have both criticised the use of DoH. Its use will allow people to circumvent Internet filters. Such as those preventing users from accessing illegal content such as copyrighted data, or images of child sexual abuse.
Organisations have also complained. They will not be able to apply corporate-level Internet filtering if users enable DoH.
Mozilla have responded to this issue. Network Service Providers and Network Administrators will signal certain capabilities. This includes content filtering which would be adversely affected by DoH. When Firefox receives such signals, it will disable DoH for the rest of the network session.
To signal to Firefox that DoH should be disabled, Network Administrators can add the following domain to their firewall block list: use-application-dns.net
Firefox will always attempt to resolve this domain. They do this using the operating system specified DNS service. If the response is NOERROR, or the response contains any A or AAAA records, then DoH will be used.
If the response is NXDOMAIN, SERVFAIL, or contains no A or AAA records, then DoH will not be used. The browser will disable DoH to allow the network to manage any DNS filtering.
If the user has set the "DoH always" preference, then this will be used, regardless of network settings. IT departments will need to ensure that they have locked the Firefox config settings: kb.mozillazine.org/Locking_preferences
Another scenario, which has caused criticism is internal IP address ranges. Some organisations may not have issues with blocking certain Internet addresses. But, they may have internal IP address ranges which cannot be resolved. They will need internal DNS.
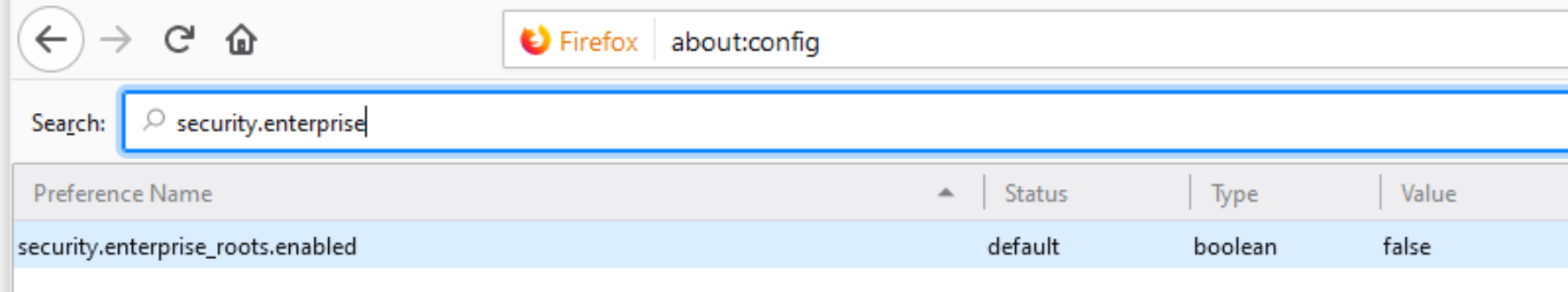
Mozilla have a solution for this in the form of an about:config setting.
If the variable security.enterprise_roots.enabled is set to true, Firefox will also disable DoH.
This setting is checked every time the browser is started. This enables the browser to detect when a device has connected to a new network. Such as moving between work and home/coffee-shop, etc.
It looks like DoH is becoming the norm for popular browsers. Organisations need to put in place policies to accommodate this new security feature.