PYSA Loves ChaChi: a New GoLang RAT
By The BlackBerry Research & Intelligence Team

The BlackBerry Research and Intelligence Team have been tracking a GoLang remote access Trojan (RAT) targeting Windows® systems which we've dubbed ChaChi. The name ChaChi comes from two key components of the RAT, Chashell and Chisel, which the malware operators used rather than creating bespoke tools.
This Trojan has been used by operators of the PYSA (aka Mespinoza) ransomware as part of their toolset.
Timeline
ChaChi has been seen in the wild since early 2020. The first known variant of ChaChi was used in attacks on the networks of local government authorities in France, and was listed as an indicator of compromise (IoC) in a publication by CERT France.
BlackBerry analysts have observed later versions of ChaChi being deployed by the PYSA operators in campaigns that have shifted to targeting educational institutions across the U.S., as reported by the FBI.
BlackBerry has responded to incidents involving PYSA ransomware where ChaChi was also identified on hosts in the victim environment. Key highlights of the PYSA campaign include:
- Defence Evasion: PowerShell scripts to uninstall/stop/disable antivirus products and other essential services.
- Credential Access: Dumping credentials from LSASS without Mimikatz (comsvcs.dll).
- Discovery: Internal network enumeration using Advanced Port Scanner.
- Persistence: ChaChi installed as a Service.
- Lateral Movement: RDP and PsExec.
- Exfiltration: Likely over ChaChi tunnel.
- Command and Control (C2): ChaChi RAT.
Fake Phishing Domain for Banco Chile
BlackBerry researchers track and monitor C2 servers using a variety of fingerprinting and discovery techniques. Analysis of networking IOCs yielded information for TTPs, which hint at ChaChi's targets.
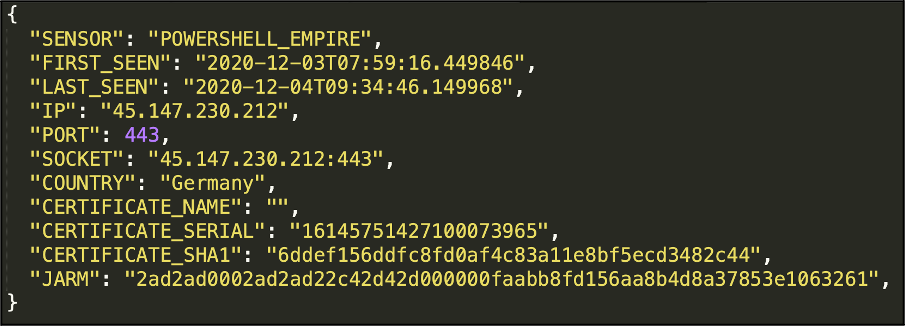
For example, one IP address appeared in one of our intelligence platforms in early December 2020 and was active for 24 hours. The IP (45.147.230[.]212) is hosted by AS30823 Combahton in Germany. It triggered one of our sensors for PowerShell Empire, artifacts of which have been observed on systems following a PYSA ransomware incident:
Screenshot 1: Alert for PowerShell Empire on public facing server.
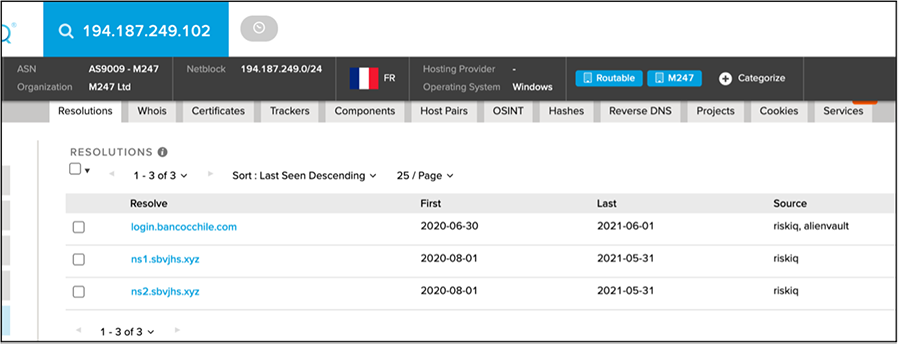
Checking the domain resolutions on the extracted IP addresses can also provide some interesting results and intelligence. The IP address 194.187.249[.]102 was extracted from a sample of ChaChi, along with a domain used as a C2 server. This domain was sbvjhs[.]xyz. Unsurprisingly, the name servers, "ns1" and "ns2" for that domain also resolve to the same IP address. Notably, the other domain that also resolves to that same IP is login.bancocchile[.]com:
Screenshot 2: ChaChi IP resolving to fake Banco Chile Domain.
The legitimate domain for Banco Chile is hosted on a ".cl" Top Level Domain (TLD) and does not have the extra "c" between the words "Banco" and "Chile". This may be a domain that was intended for malicious purposes:
- A phishing domain targeting employees or customers of Banco Chile.
- A domain used to stage/deliver ChaChi RAT.
Coincidentally, both nameserver domains and the fake Banco Chile domain were active before, during, and after the reported breach at another Chilean bank (Banco Estado), reported in September 2020 and attributed to REvil ransomware.
Read the BlackBerry Research & Intelligence Team’s full writeup on ChaChi here.