How Smart Is Your SOAR Platform?
By Dan Verton
How smart is your Security Orchestration, Automation, and Response (SOAR) platform? The answer to that question is critical to determining how protected your organization is from the next data breach or ransomware attack.
Imagine for a moment that you're sitting at the bar in Caesar's Palace between Black Hat sessions and you receive an email from your boss, the Chief Information Security Officer, that says he/she not only wants to be made instantly aware of potential incidents that could lead to a data breach or ransomware attack on your company's new clinical trial database but he/she also wants to ensure that the new state-of-the-art threat library developed by the CTI team can drive better decisions and execute controls automatically based on changes in the threat landscape.
Did you make the right investment decisions? Is your SOAR smart enough to handle that?
While most garden variety orchestration and automation platforms can speed up a repetitive process and carry it across tools, they're often limited to so-called dumb tasks — those that require no intelligence.
ThreatConnect SOAR combines threat intelligence, analytics, and orchestration into one place to enable faster, more informed decisions. Because threat intelligence is baked in, there's no need for complicated data manipulation or time-intensive lookups: it's all converted to a predictable and easily understood format while still preserving the source's attribution information and reputation details.
ThreatConnect's intelligence-driven SOAR helps security teams capture, correlate, and make decisions based on high-fidelity intelligence relevant to your organization. Analysts can leverage data from ThreatConnect's CALTM (Collective Analytics Layer) to gain more insight from thousands of ThreatConnect users around the globe on intel-related artifacts such as IP addresses, emails, or URLs. Security teams can add those artifacts back into ThreatConnect's intelligence repository to help during future investigations and across other team initiatives. Likewise, incident responders can adjust decisions on the fly based on the changes seen in the intelligence that is influencing the process.
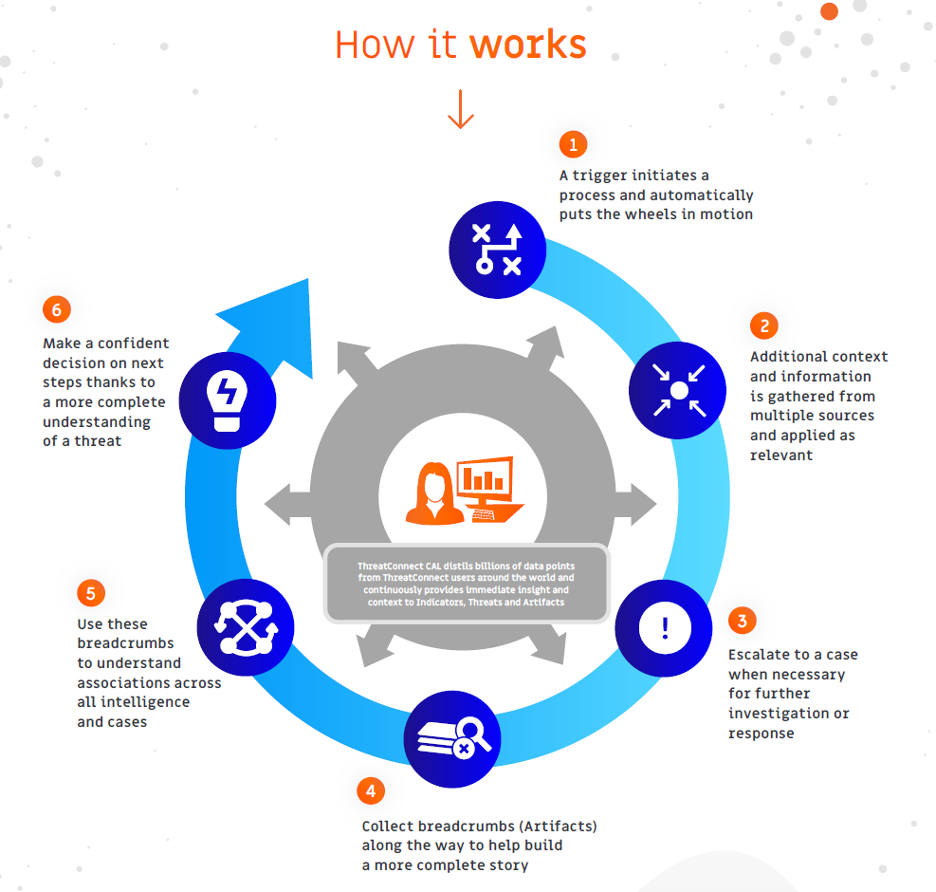
Using threat intelligence and orchestration together, situational awareness and historical knowledge determine what processes should be handled and how. Threat intelligence allows the process to automatically adjust itself and helps you drive further decision-making. Taken one step further, threat intelligence allows analysts to cross-reference what they observe with historical knowledge and situational awareness. This insight enables decisive action — an action that can then be automated and placed into your security team's muscle memory. Using threat intelligence to determine automation empowers you to be proactive in mitigating threats to your organization.
ThreatConnect bridges the gap that too often exists between threat intelligence and security operations, allowing security teams to fully make use of their current investments by automating repetitive tasks, prioritizing critical events, and providing the situational awareness and additional context needed to inform decision making that will better protect your organization from attacks.
Want to learn more? Visit threatconnect.com


