How AI Interrupts Ransomware At its Earliest Stages, Without Disrupting Normal Operations
By Toby Lewis, Head of Threat Analysis
With the ransomware crisis reaching critical levels, many organizations are struggling to stay ahead of attackers. Back-ups no longer provide a meaningful way out, as threat actors will exfiltrate sensitive data in addition to encrypting files and systems. In these 'double extortion' attacks, criminals then threaten to release stolen data.
The decision to pay or not to pay ransom is also becoming increasingly vexed. The financial costs of disruption and downtime, along with the reputational cost of a high-profile incident, tend to dramatically outweigh the cost of paying ransom. Ransomware threat actors know this, which is why they continue to be largely successful.
Ideally, rather than rely on remediation and response after the ransomware detonates, these threats would be dealt with proactively, at their earliest stages, before the damage is done. And while ransomware attacks seemingly happen in seconds—with files and systems suddenly locked down with a note attached—there are always subtle forms of unusual behavior that occur days and even weeks before the ransomware strikes.
Before a threat actor deploys ransomware, they will always have a point of initial intrusion, and then spread laterally as stealthily as possible to gain maximal leverage, locating the most critical files and systems. To blend in, attackers often use legitimate tools, such as remote access management, in what is known as 'living off the land.'
Self-Learning AI is uniquely positioned to autonomously detect, investigate, and respond to these pre-cursors to ransomware, cutting through the noise to identify threatening activity, no matter how subtle the unusual behavior. Even when attackers employ bona fide tools, Darktrace's Self-Learning AI draws on its dynamic understanding of normal, formed by multiple layers of machine learning, to pinpoint unusual behavior.
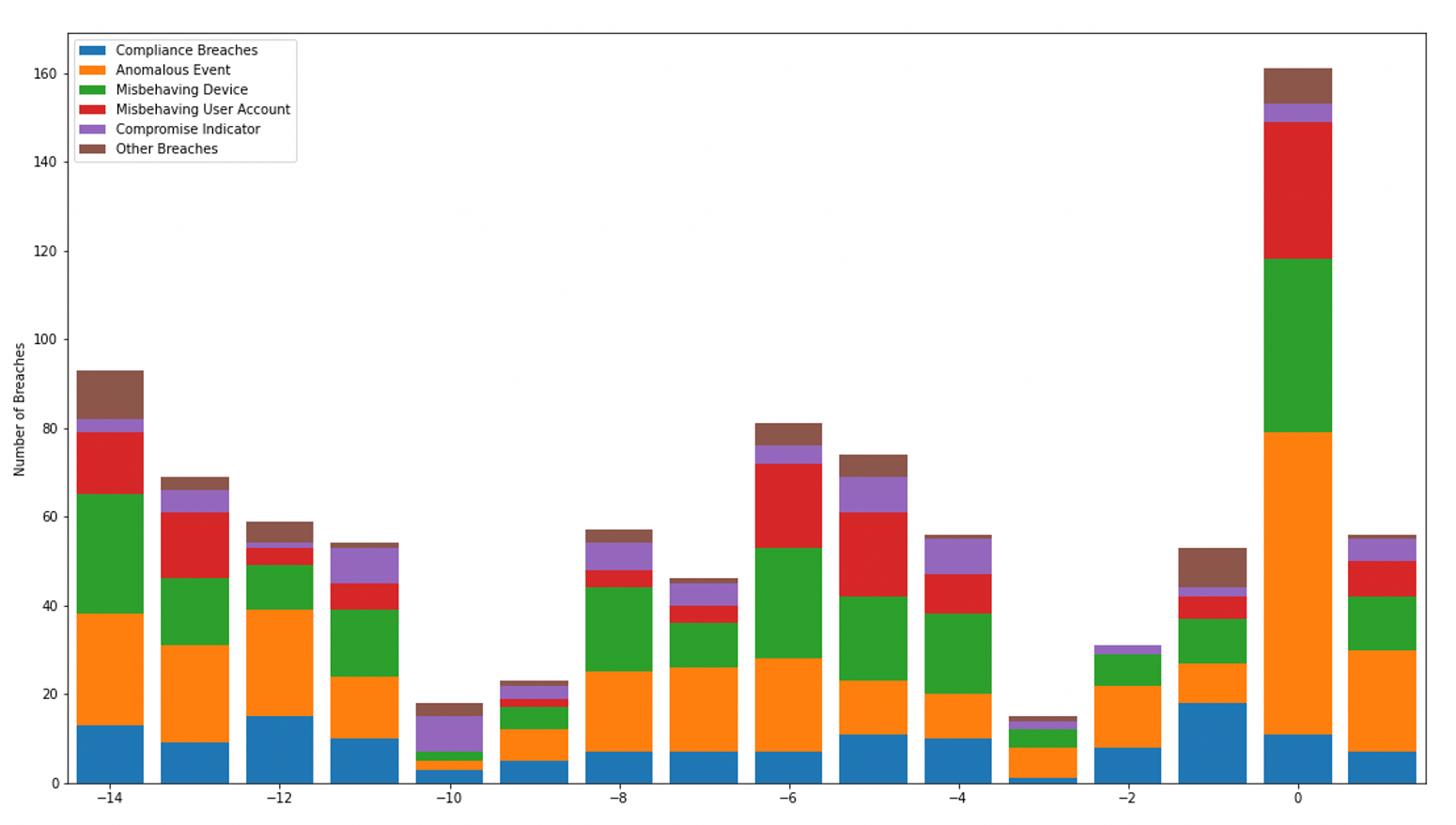
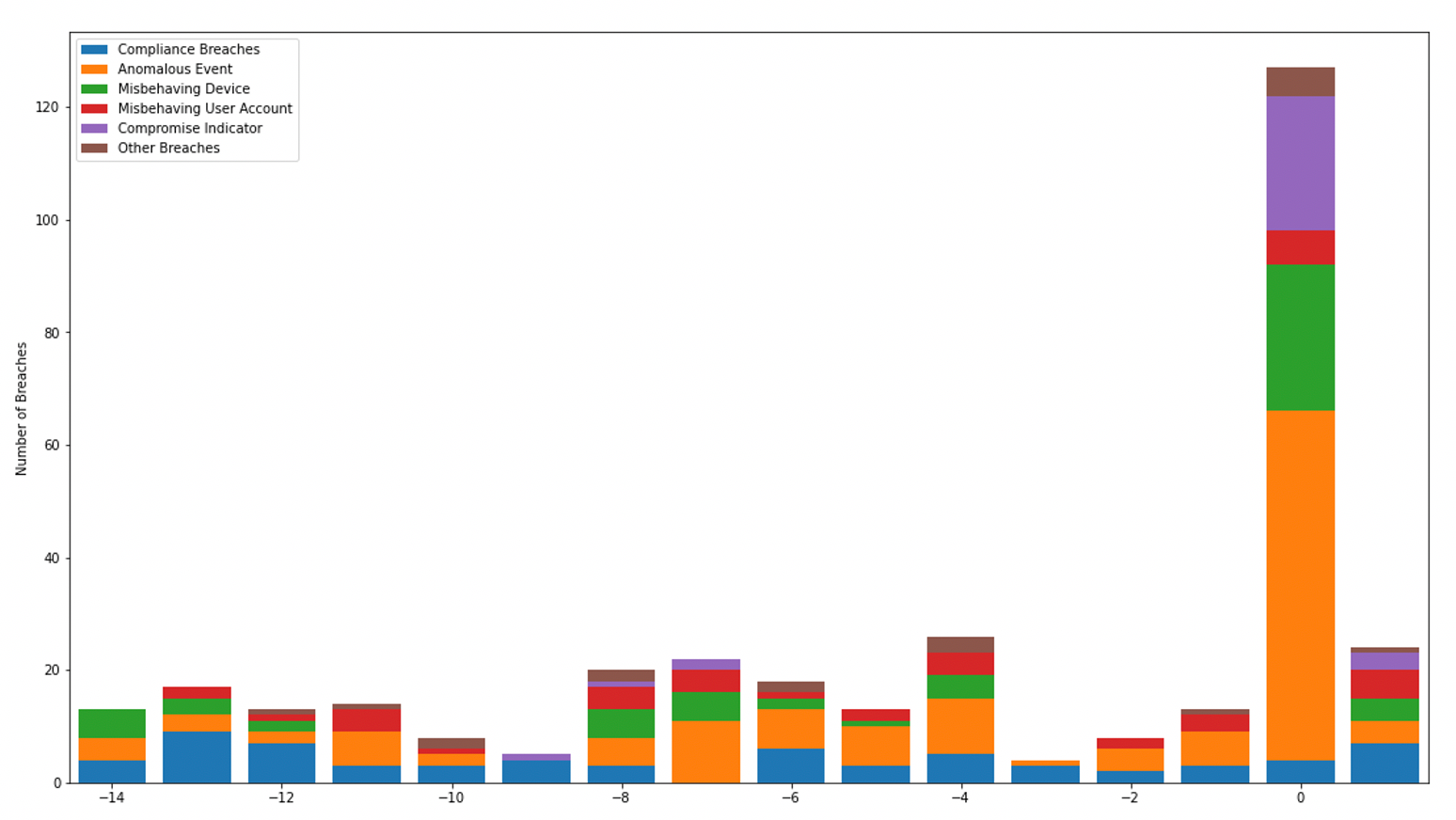
With this precise understanding of 'normal', the AI can then take highly targeted action to interrupt the ransomware, without disrupting legitimate activity. In fact, in a number of recent cases, Darktrace detected multiple significant events in the run-up to the ransomware event. In some of those cases, Darktrace's Autonomous Response technology wasn't yet enabled, such that the attack was allowed to continue. Here, we can see just how effective Darktrace is in reacting to early stages, preventing doomsday scenarios from ever materializing.
In multiple instances, the precursory activity would have resulted in the triggering of intervention by Autonomous Response over 60 times. There is also at least one instance of a higher fidelity machine learning detection into the Darktrace SOC for manual alerting to the customer, notably, 10 days prior to the deployment of ransomware.
With ransomware increasingly targeting critical infrastructure and global supply chains, it has never been more important to detect, investigate, and respond to threats at their earliest stages, before they can escalate into crisis. Darktrace's Self-Learning AI, with its ability to understand 'normal' behavior and immediately detect and neutralize threats—and also reduce triage by up to 92% with automating investigations—nips these threats in the bud in a matter of seconds.
Case 1
Case 2