EDR Solutions Require Comprehensive Telemetry to Fend Off Multi-Vector Attacks
By Hiep Dang, Vice President of Endpoint Security Solutions, Qualys
Endpoint devices are under increasingly aggressive and sophisticated attacks, so protecting them effectively from cyber criminals has become a thorny and vexing challenge as the threat landscape expands. It doesn’t help that endpoint protection today fluctuates between two strategies that are diametrically opposed yet equally ineffective. One relies narrowly and myopically on endpoint anti-malware software, a traditional tactic that offers little visibility into what’s going on in devices and that every day proves more and more unsuccessful. The other more recent strategy is costlier and more complex and swings to the other extreme: Stacking up on disjointed point tools and creating large incident response teams to sift through mounds of siloed data. This leads to an abundance of false positives, and to slow and misguided responses.
Solving the EDR Conundrum
Keeping endpoints secure and compliant requires a cloud-based, holistic approach for gathering comprehensive context not only about the devices but also about their IT environment. With broad visibility and deep insights, security teams can quickly and precisely predict, prevent, detect and respond to endpoint attacks in a continuous loop of monitoring and assessment. It creates a perpetual cycle of constant improvement within your corporate environment.
This was the goal that guided Qualys as it developed its EDR solution and anchored it on multiple context vectors that give security teams a unified, always updated view into the entire attack chain.
The Qualys Approach to EDR
Qualys Multi-Vector EDR unifies a full set of vectors for 360-degree context, including asset discovery, detection of vulnerabilities and misconfigurations, in-depth endpoint telemetry and network visibility.
The solution leverages the Qualys Cloud Agent, a versatile, lightweight agent that works across multiple Qualys security and compliance apps, reducing complexity and lowering costs. The Cloud Agent is constantly collecting IT, security and compliance data from endpoints and beaming it to the Qualys Cloud Platform, where it's correlated, prioritized and analyzed.
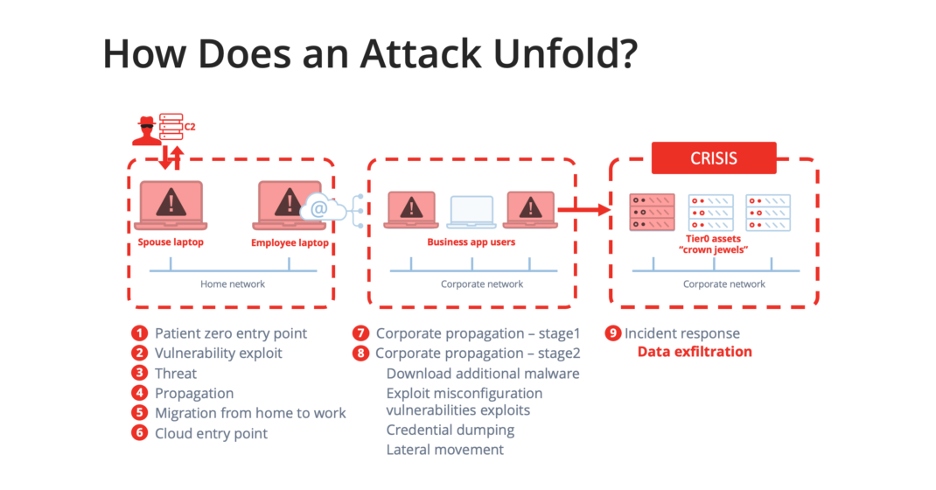
Anatomy of an Attack
With Qualys Multi-Vector EDR, security teams get unimpeded visibility and real-time insights not only into endpoints but also across the entire network, and can take whatever action is appropriate, whether it’s killing a process, quarantining files, deploying patches, fixing misconfigurations, or something else. It gives you this correlation, aggregation and contextually-rich data that allows you to answer those basic fundamental questions: what, where, who, when, how, and most importantly, why.